
Instead of storing their credentials locally, the organization trusts an external identity provider (IdP) — such as Google, Microsoft Entra ID (Azure AD), Okta, Ping, or a partner’s SAML-based system — to verify users’ identities.
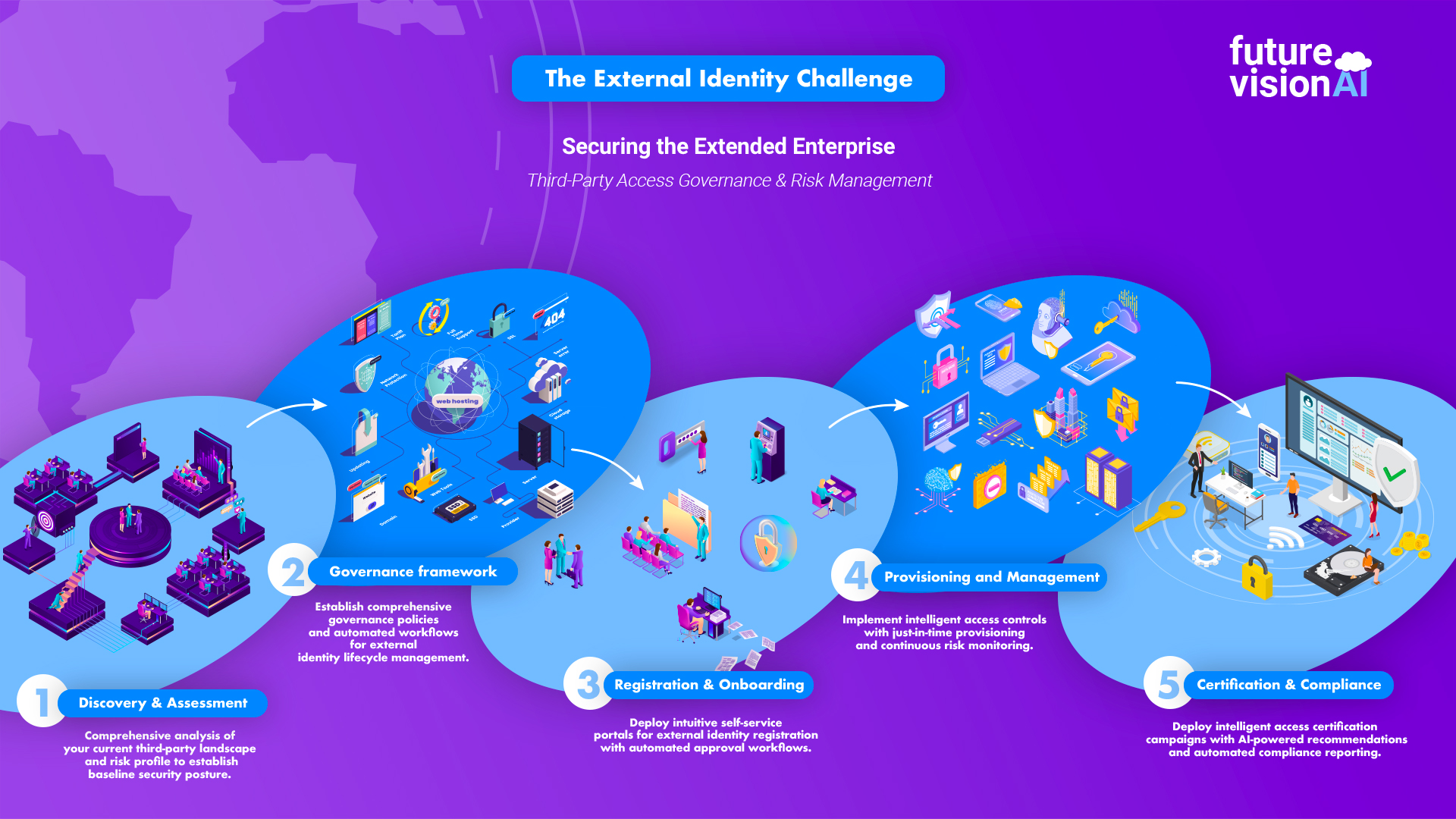
1. User Accesses Resource
The user tries to access an application or cloud service (the Service Provider).
2. Redirection to Identity Provider
The SP redirects the user to the configured external IdP for authentication (e.g., Okta, Google, Azure AD).
3. Authentication at IdP
The user enters credentials on the IdP’s login page.The IdP authenticates them using its own method — password, MFA, biometrics, etc.
4. Assertion/Token Issued
Once authenticated, the IdP generates an assertion (SAML) or token (OIDC/JWT) containing :
- User identity information (claims)
- Signature and timestamp
- Optional role or group mappings
5. Assertion Sent to SP
The assertion/token is sent back (via browser redirect or API call) to the Service Provider (IAM system).
6. Token Validation
Achieve zero trust security with automated controls
The SP validates:
- The signature (to ensure it’s from the trusted IdP)
- The expiration time
- The audience (intended recipient)
- Any attributes required for authorization
7. Access Granted
Achieve zero trust security with automated controls
After successful validation, the SP:
- Creates a temporary session for the user
- Assigns permissions based on roles, groups, or claims
- Logs the authentication event